What is Cross Site Scripting?
Cross-site scripting (also known as XSS) is a web security vulnerability that allows an attacker to compromise the interactions that users have with a vulnerable application. Cross-site scripting vulnerabilities normally allow an attacker to masquerade as a victim user, to carry out any actions that the user is able to perform, and to access any of the user's data. If the victim user has privileged access within the application, then the attacker might be able to gain full control over all of the application's functionality and data.
How does XSS Works?
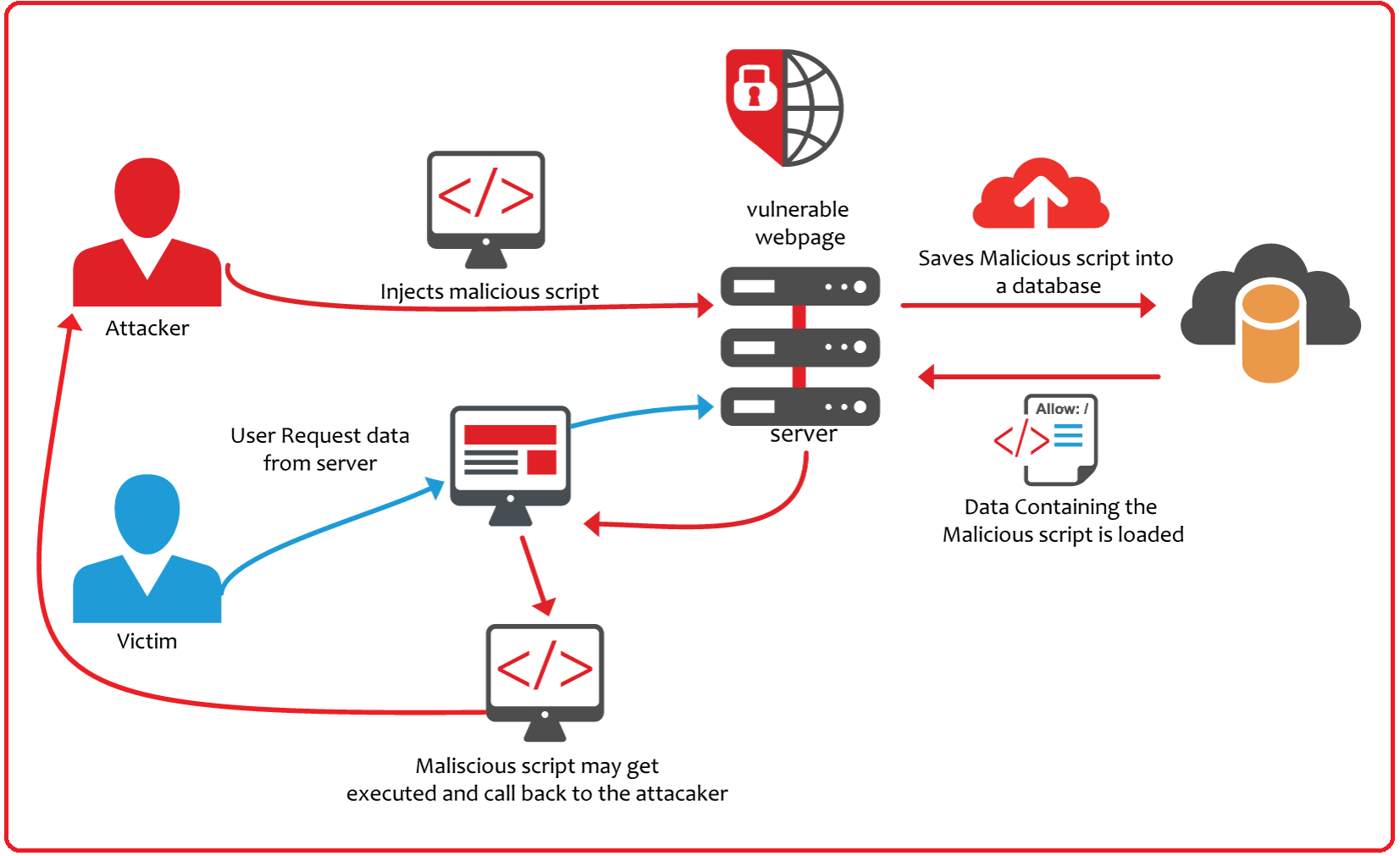
Cross-site scripting works by manipulating a vulnerable website's source code/storage system so that it returns malicious JavaScript to users. When the malicious code executes inside a victim's browser, the attacker can fully compromise their interaction with the application by stealing session cookies, user credentials, tokens, secrets, etc.
Types of XSS
- Reflected XSS: The malicious script comes from the current HTTP request when injected in the source code of the application.
- Stored XSS: The malicious script comes from the website's database which eventually gets executed in user's browser.
- DOM-based XSS: The vulnerability exists in client-side code rather than server-side code. In DOM-based XSS, the malicious user input goes inside the source and comes out of the sink.
Severity
The Stored XSS has a severity of P2 with a CVSS score of 7-8.9 which is High. This type of XSS can be used to steal cookies of large number of users or even admin as well, because everytime someone loads the page they get affected by this.
Exploiting Cross-Site Scripting
Test every entry point which stores values in the server.
Refer the XSS Documentation.
Check for a popup on the screen.