What is Steganography?
Steganography is the technique of hiding secret data within an ordinary, non-secret, file or message in order to avoid detection; the secret data is then extracted at its destination. The use of steganography can be combined with encryption as an extra step for hiding or protecting data. The word steganography is derived from the Greek words steganos (meaning hidden or covered) and the Greek root graph (meaning to write). Steganography can be used to conceal almost any type of digital content, including text, image, video or audio content; the data to be hidden can be hidden inside almost any other type of digital content. The content to be concealed through steganography -- called hidden text -- is often encrypted before being incorporated into the innocuous-seeming cover text file or data stream. If not encrypted, the hidden text is commonly processed in some way in order to increase the difficulty of detecting the secret content.
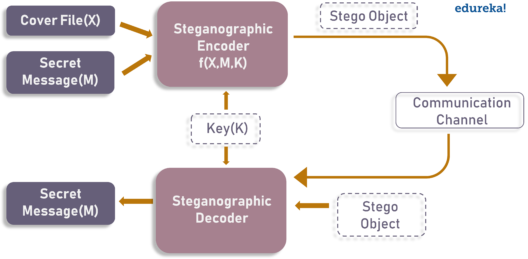
How does Steganography Works?
There are literally dozens of ways to hide messages, and each one works differently. But most steganography experts rely on the same principles to do their work. Steganography relies on several pieces, including:
-
=> Payloads. What do you want to embed or hide?
-
=> Carriers. What file or asset will hide your payload?
-
=> Package. How will the carrier look or respond when buried with the payload?
-
=> Key. How will the recipient decode your message and find the payload?
Types of SQL Injection
- In-band SQLi (Classic SQLi) : In-band SQL Injection occurs when an attacker is able to use
the same
communication channel to both launch the attack and gather results.
- Error-based SQLi : Error-based SQLi is an in-band SQL Injection technique that relies on error messages thrown by the database server to obtain information about the structure of the database.
- Union-based SQLi : Union-based SQLi is an in-band SQL injection technique that leverages the UNION SQL operator to combine the results of two or more SELECT statements into a single result which is then returned as part of the HTTP response.
- Inferential SQLi (Blind SQLi) : In an inferential SQLi attack, no data is actually
transferred via the web
application and the attacker would not be able to see the result of an attack in-band.
- Boolean-based (content-based) Blind SQLi : Boolean-based SQL Injection is an inferential SQL Injection technique that relies on sending an SQL query to the database which forces the application to return a different result depending on whether the query returns a TRUE or FALSE result.
- Time-based Blind SQLi : Time-based SQL Injection is an inferential SQL Injection technique that relies on sending an SQL query to the database which forces the database to wait for a specified amount of time (in seconds) before responding.
- Out-of-band SQLi: Out-of-band SQL Injection occurs when an attacker is unable to use the same channel to launch the attack and gather results.
- Voice Based Sql Injection:It is a sql injection attack method that can be applied in applications that provide access to databases with voice command. An attacker could pull information from the database by sending sql queries with sound.
Severity
SQL injection can be categorized as P1 or P2 bug with a CVSS score of 7.5 - 9 which is High.
Exploiting SQL Injection
Test every entry point on a target website.
Refer the SQL Injection Documentation.
Check for sql errors on the screen.