What is CORS?
Cross-origin resource sharing (CORS) is a browser mechanism which enables controlled access to resources located outside of a given domain. It extends and adds flexibility to the **same-origin policy**. However, it also provides potential for cross-domain based attacks, if a website’s CORS policy is poorly configured and implemented. The CORS protocol uses some HTTP headers that define trusted web origins and associated properties such as whether authenticated access is permitted. Many modern websites use CORS to allow access from **subdomains** and **trusted third parties**. Sometimes because of mistakes of developers attacker can use the misconfiguration to exploit the vulnerability.
How CORS Works?
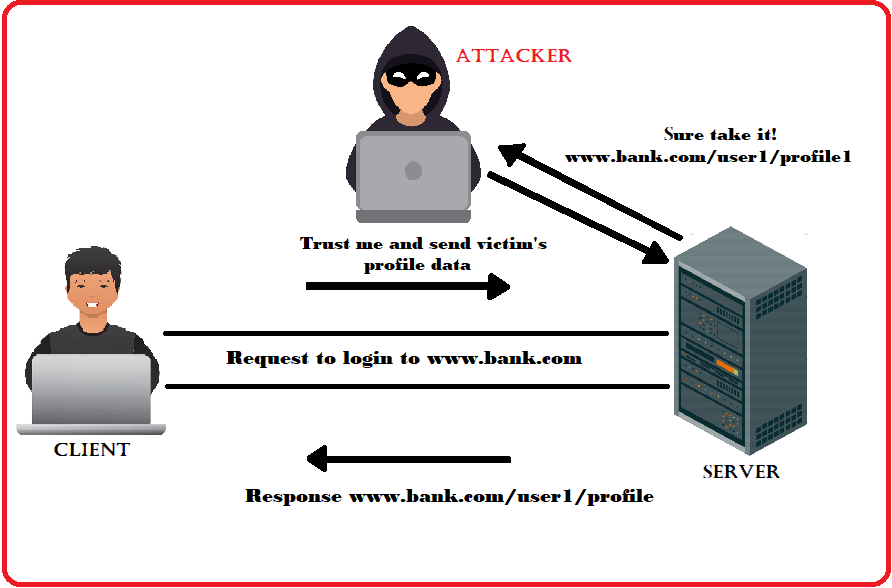
In normal situations, The client request the server to login to www.bank.com. The server validates the client and in response sends the client's profile which is `www.bank.com/user1/profile` to display it on the browser. If the CORS policy is not properly set, the attacker can disguise himself and tells the server to trust the Attacker and send the victims data of profile. The server in turn trusts the Attacker and sends the client's profile to the Attacker. Thus the attacker succeeds in getting sensitive data of the Client.
Severity
The severity of CORS varies and depends on case to case basis. In a situation where PII is leaked CORS can be categorized as P3 or P2 bug with a CVSS score of 7 - 8.9 which is High.
Rules for Exploiting Cross-origin Resource Sharing
Capture the request in Burp and add a customer header called as "Origin".
Use Origin Upskillr.co for bonus points.
Check out the response. Use the exploit code and exploit CORS.